UT Foundation Policies
1.6 Digital Strategy & Innovation
EFFECTIVE: 6/22/2011 · REVISED: 6/22/2011
General Purpose
The University of Tennessee Foundation, Inc. (UTFI), through The University of Tennessee, licenses the Encompass Online Community (the site) to manage UTFI’s online giving programs. This document sets forth policies governing the implementation and use of the Encompass online giving system at UTFI.
Types of Information that May be Collected
Only personal information provided by the donor will be collected via the site.
How Information May be Collected and Used
Personally-identifiable information will not be sold or otherwise transferred to unaffiliated third parties without the approval of the donor.
Notification of Changes and Donor Acceptance of the Policy
UTFI will not use personally-identifiable information provided by a donor in a manner different from that stated at in the policy posted on the site at the time the information was collected without first notifying the donor.
Refund Policy
The Director of Gift Records will review and, if appropriate approve, all donor requests for refunds. Processing of refunds will be handled in accordance with 1.4.8 Credit Card Processing.
EFFECTIVE: 6/22/2011 · REVISED: 3/18/2020
Overview
Anthology Encompass is certified as a Level 1 Service Provider under the Payment Card Industry Data Security Standard (PCI DSS).
The Payment Card Industry Data Security Standard (PCI DSS) was developed by the founding payment brands of the PCI Security Standards Council, including American Express, Discover Financial Services, JCB International, MasterCard Worldwide and Visa Inc. Inc. International. The PCI DSS is a set of comprehensive requirements for enhancing payment account data security that was developed to help facilitate the broad adoption of consistent data security measures on a global basis.
The PCI DSS includes requirements for security management, policies, procedures, network architecture, software design and other critical protective measures. This comprehensive standard is intended to help organizations proactively protect customer account data. The PCI Security Standards Council is the organization whose mission it is to enhance payment account data security by driving education and awareness of the PCI Security Standards. The organization was founded by American Express, Discover Financial Services, JCB International, MasterCard Worldwide, and Visa, Inc.
EFFECTIVE: 6/22/2011 · REVISED: 3/18/2020
Overview
The UT Foundation staff will use the Encompass Event Management feature (the site) to manage online registration and payment for Alumni and Development events. This document sets forth policies governing the implementation and use of the Encompass event management system at UTFI.
How Information May Be Collected and Used
Personally identifiable information collected on the site will not be sold or otherwise transferred to unaffiliated third parties without the approval of the person who provide the information.
Refund Policy
Before the checking account administrator processes a refund, the refund must be reviewed and approved in writing by a program director or assistant/associate vice chancellor within the checking account administrator’s department. Processing of refunds will be handled in accordance with 1.4.8 Credit Card Processing.
Policy Maintenance
UTFI staff will review this policy annually for content and accuracy. Changes will be made to this policy as deemed necessary.
In addition to reviewing this policy, the Director of Gift Records will annually ensure that Elavon still maintains its VISA CISP/PCI compliance. This is verified through the following steps:
- Go to the Visa PCI Compliance website: https://usa.visa.com/support/small-business/security-compliance.html
- Search the Visa Global Registry of Service Providers: https://usa.visa.com/splisting/splistingindex.html
Reconciliation Policy
Each alumni office is responsible for reconciling its event transactions against Virtual Merchant account(s) each business day. At least two alumni office employees will be involved in the reconciliation process. Transactions are automatically settled nightly by Elavon. Each morning one employee will produce the daily transaction report from Encompass and submit that report to the checking account administrator to reconcile. Under no circumstances should only one employee be involved in the reconciliation process.
EFFECTIVE: 6/22/2011 · REVISED: 5/18/2022
Overview
The University of Tennessee Foundation Inc (UTFI), through The University of Tennessee, licenses Anthology Encompass Online Community (the site) for a variety of purposes, including online giving, online event registration and payment, and online communications management. The site incorporates reasonable measures to protect and keep information secure. For example, Secure Socket Layer or “SSL” and firewalls are used to protect information from loss, misuse and alteration.
Only those UTFI employees who require access to information to carry out legitimate UTFI business functions are allowed access to data collected by and stored in Encompass.
Security policies will be reviewed periodically and revised as required.
All credit card information is processed via Elavon’s Payment Gateway, which is seamlessly integrated with the Anthology Encompass and is compliant with PCI DSS and PA DSS. See 1.6.2. PCI Compliance Certificate.
The Director of Constituent Management will annually ensure that Elavon still maintains its VISA CISP/PCI compliance. This is verified through the following steps:
- Go to the Visa PCI Compliance website: https://usa.visa.com/support/small-business/security-compliance.html
- Search the Visa Global Registry of Service Providers: https://usa.visa.com/splisting/splistingindex.html
EFFECTIVE: 4/12/2011 · REVISED: 3/18/2020
Fonts / Typography
When working in the main content areas of your Encompass website, you will seldom (if ever) have a reason to use the font format tools. Instead, each site has a predetermined set of type styles.
Off limits! Do not use these tools!
![]()
Reasons for using pre-determined styles
- Consistency of Brand – Each of our sites has its own campus or system branding, but they are also unified by certain graphical elements, including typography. The goal was to create a “family” of UT alumni websites, and we need to protect that unity.
- Cleanliness – The pre-determined styles control not only font selection, weight, and color but also leading (line height) and kerning (spacing between letters). Playing with these characteristics “muddies” up a page.
- Search Optimization – When search engines review the content of a page, they prioritize text that has been made a header. Bolding “Student Programs” doesn’t teach a search engine very much, but if “Student Programs” is a Heading1, those are the two most important words on the page.
- Universal Changes – If we use styles consistently, we can make site-wide changes in seconds rather than hours. For example, if we decide we no longer want Heading3 to be bolded, we can change a single line of code rather than having to edit every individual page.
Choosing the right style
This is the dropdown box you’re looking for:
![]()
By default, it will say “Normal.” If you’ve copied and pasted from another website, it might instead say “Paragraph Style.” This is the standard style that should be used for all basic content.
Headings
Headings should be used first as an organizing tool. Think of each page as if it were broken down into a traditional content outline:
- Heading 1
- Heading 2
- Heading 2
- Heading 3
- Heading 3
- Heading 4
- Heading 4
- Heading 2
- Heading 2
Heading 1 – The title of the page. Encompass will automatically insert the name of each page between H1 tags. In general, you should never select Heading1 from the dropdown, because there should only be one H1 on each page.
Heading 2 – An H2 is a sub-section of an H1. Use Heading2 to create distinct sections on a single page.
Heading 3 – An H3 is a sub-section of an H2. In general, you should never use Heading3 unless it falls under a Heading2.
Heading 4 & Heading 5 – These follow the same pattern. H4 is a sub-section of H3; H5 is a sub-section of H4. In general, you’ll very seldom have a reason to use Heading4 or Heading5.
In-line emphasis
- Italicize words for emphasis. For example: “There was never a day that I did not look forward to teaching.”
- Bold words to call attention to them. For example: “Chapter forms are due on March 15.”
- Never underline or re-color text. Users will think it’s a hyperlink.
Photos and Images
Encompass makes it very easy to upload a photo and place it in a content area, but properly adding and formatting an image for a website takes a little more work.
Sizing Matters
The size of a web image can be controlled in two ways:
Actual file size
The actual size of an image is measured in pixels. For example, a photo that is 1000 pixels wide by 800 pixels tall will be approximately 150kb. The same photo shrunk to 100×80 pixels is less than 5kb. The more pixels, the more sharpness, detail, and clarity.
Coded dimensions
Images are inserted into a webpage by an HTML tag. For example, the following:
<img src=”flower.jpg” width=”600” height=”480” />
Will display as:

But the same image will display very differently if it’s called by the following code:
<img src=”flower.jpg” width=”600” height=”180” />

Here’s the important part: Even though the second line of code is telling the image to only display 180 pixels tall, the entire photo is downloaded from the web server to the user’s browser. Which means that even the tiny image below is 40kb:
<img src=”flower.jpg” width=”10” height=”8” />
![]()
Here’s the other important part: A website image will also be distorted if the actual file size is significantly smaller than the coded dimension. For example, if the actual flower photo is 100×80 pixels (5kb) and is set to display at 1000×800 pixels, it will look like this:

Best practice: Actual file size should equal the coded dimensions.
In order to avoid distortion and the downloading of unnecessarily large images, you should always crop photos to the exact size that you wish for them to be displayed.
And don’t stretch images either.

Sizing, Formatting, and Positioning Images
So, the goal is to crop images to the exact size you want them to display before uploading them into Encompass. How big should they be?
Maximum width
The Encompass template pages have predetermined content areas that are set to specific widths. If you exceed the maximum width, you’ll probably break the page (especially if an alum is viewing the site in an old web browser). So don’t exceed the maximum width.

Warning: Borders add width
When you insert an image, you’ll have the option of adding a solid grey border around it (more on this below). The border will add 10 pixels to the total width, so remember to compensate by making the maximum width 650 pixels for the one-column template and 410 pixels for the two-column template.
Maximum/suggested height
Technically, there’s no such thing as maximum height. I could insert an image that is 10,000 pixels tall and make the user scroll and scroll and scroll to see it all. However, as a general rule try to avoid images that are taller than 350 pixels. Any larger than that and alumni who are using older monitors with lower screen resolutions will have to scroll to see the bottom of the image. For horizontal images, the suggested height is 230 pixels.
Image Properties
Encompass allows us to adjust the properties of an image before inserting it, but, in general, we won’t be using these tools.
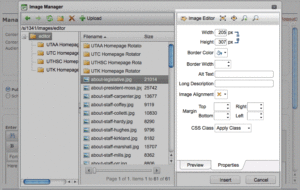
- Width & Height: Adjusting these will change the image’s coded dimensions and will distort it.
- Border Color & Width: We’ll use styles to control this.
- Alt Text/Long Description: These fields determine what seeing-impaired alumni will hear when they browse our sites with assistive technology. It’s important to include a text description of each photo you insert.
- Image Alignment & Margin: We’ll use styles to control this.
- CSS Class: This doesn’t work like one would assume it should, so just ignore it.
Styling Photos
Why are we styling photos instead of tweaking them via the properties editor? For the same reasons we are using styles to control typography: consistency, cleanliness, and the ease of making universal changes.
Step 1: Insert the photo and use the properties editor to add Alt Text and a Long Description.
Step 2: Switch from the Design view to the HTML view. These buttons can be found at the bottom of the content editing screen.
![]()
Step 3: Where the photo has been inserted, you’ll see a line of code like this:
<img longdesc=”A photo of the Tennessee capitol building” alt=”A photo of the Tennessee capitol building” style=”” src=”/s/1341/images/editor/about-legislative.jpg”>
Step 4: Add the appropriate class.
- photo-border – puts a grey border around the image
- photo-left – floats the image to the left and adds a 15-pixel margin to the right and bottom
- photo-left-border – floats the image to the left and adds a margin and border
- photo-right – floats the image to the right and adds a 15-pixel margin to the left and bottom
- photo-right-border – floats the image to the right and adds a margin and border
The new line of code will look like this:
<img longdesc=”A photo of the Tennessee capitol building” alt=”A photo of the Tennessee capitol building” style=”” src=”/s/1341/images/editor/about-legislative.jpg” class=”photo-rightborder”>
Step 5: Click “Save.”
EFFECTIVE: 4/12/2011 · REVISED: 6/22/2011
Overview
The University of Tennessee Foundation (UTFI) and UT Alumni Association (UTAA) do not sell alumni information to 3rd parties. All alumni information is strictly guarded for use by individual alumni, UTFI and UTAA for personal, UTFI and University-related purposes only.
UTFI will take all reasonable measures to secure the personal information available through the UTAA Online Community (the site). The site shall be password protected to allow access by registered University alumni and staff only. Because a certain degree of privacy risk is encountered any time information is shared over the Internet. The site shall also allow registered users the ability to hide their information from being viewed by other community members.
Guidelines for Use
Users of the site shall be required to abide by the following rules and regulations:
- Unauthorized copying, reproduction, republishing, uploading, downloading, posting, transmitting or duplicating any of the material available on the site is prohibited. Users may download or copy any downloadable materials displayed on the site for home, noncommercial and personal use only provided, however, that the user maintains all copyright, trademark and other notices contained in such material and agrees to abide by all additional copyright notices or restrictions contained in any material accessed through the site.
- Use of information or communications available through the site for any commercial, public or political purposes is strictly prohibited. Prohibited activities include, but are not limited to, solicitations for commercial services, cold-calling of any kind or mass-mailings for commercial purposes. Information available through the site may be used for specific personal, Foundation and University-related purposes only.
- Users shall not restrict nor inhibit any other user from enjoying any service on the site. Users shall not upload, transmit, distribute or otherwise publish any materials containing a virus or any other harmful component. Posting of obscene materials or use of obscene language, posting of vulgar materials or use of vulgar language, or use of abusive, defamatory, profane, or threatening language of any kind, constitute a violation of these policies governing the use of the site and will result in revocation of the user’s login ID and password.
- All aliases adopted by site users are subject to approval by UTFI. The University and/or UTAA.
Registered users shall be informed that neither UTFI, the University nor the UTAA is responsible for screening communications in advance and neither UTFI, the University nor the UTAA will actively monitor the use of the site. For this reason, registered users of the site shall be encouraged to report any abuses or misuse of the site to the UTAA.
UTFI, the University and the UTAA reserves the right, in their sole discretion, to take action against any user who violates this policy and/or any applicable laws and regulations, such action including but not limited to expelling the user, denying a user further access to the site, reporting the user to authorities and/or instituting legal action against the user.
Effective: 7/1/2023
Objective
To provide guidelines for texting constituents in the execution of official UT Foundation business.
Applicability
The University of Tennessee Foundation, Inc. (UTFI) texting policy applies to any UTFI-affiliated person who communicates to large groups of people in the University community via text messaging for an official UTFI purpose. This includes text messages sent from:
- A UTFI-owned device, account, or office.
- Text messages sent through third-party services on behalf of any unit of UTFI.
- Text messages from any authorized UTFI employee or agent acting in their official capacity.
This policy applies to any text messaging application or system purchased, administered, and/or created with UTFI resources that sends batch messages to 50 or more recipients.
No other texting system may use UTFI’s name, logos, name plates, icons, branding or any other UTFI indicia without written permission from the UTFI Senior Director of Communications.
It must be clear from the content of the message being sent that the message is from UTFI so that the recipients can see immediately from where it originated.
Opt-In Requirement
In accordance with the Federal Communications Commission (FCC) and the Telephone Consumer Protection Act (TCPA), only those individuals who have opted in will receive text messages from UTFI:
In 2012, the FCC revised its regulations to require telemarketers to (1) no longer allow telemarketers to use an “established business relationship” to avoid getting consent from consumers, (2) obtain prior express written consent from consumers before making calls with an autodialer or that contain a message made with a prerecorded or artificial voice, and (3) require telemarketers to provide an automated, interactive opt-out mechanism during each of the type of calls mentioned above in “(2)” so that consumers can immediately tell the telemarketer to stop calling.
Emergency and Non-Emergency Situations
In emergency situations, UTFI may lawfully send automated texts to wireless phone numbers without consent. An emergency situation is one that potentially affects the health and safety of UTFI staff and constituents.
UTFI may send non-emergency messages that are closely related to UTFI’s mission if the recipient has previously given express consent. UTFI non-emergency text messages must, at a minimum, comply with the following:
- Be only sent to those individuals who have opted in.
- Comply with applicable laws and regulations to reduce institutional risk.
- Follow best practices outlined by professional organizations.
- Allow subscribers to opt out of receiving non-emergency messages at any time.
- Communicate that standard data and text messaging rates may apply.
Each mass text message should include information on how to opt out of future text communications.
Mass text messaging must not be used to communicate:
- Personal matters, e.g., items for sale, farewell messages, etc.;
- Advertising or other commercial purposes; or
- Personal or confidential information, including, but not limited to, Social Security numbers, passwords, financial information, or grades.
Types of Messaging
The types of text messages that can be sent to UTFI constituents include:
- Giving requests: Giving Day information, initiative-specific gifts, stewardship, cultivation, etc.
- Donor recognition: Acknowledge past donations, share how gifts support the institution, special initiatives, etc.
- Constituent engagement: Networking events, regional events, homecoming celebrations, volunteer management, mentoring students, bio demo collection efforts, etc.
Implementation and Communication
Each unit that uses text communications must disseminate this Policy and the procedures/parameters set forth by UTFI to its staff who will be sending text messages.
Texts messages/responses received from Constituents should be responded to within 72 hours.
System Administrators are responsible for configuring their platforms to comply with this Policy.
System Administrators must maintain an up-to-date list of those individuals who have opted out of receiving non-emergency text messages.
System Administrators must develop a method for saving text messages and responses as necessary to comply with applicable document retention requirements.
Privacy
The UT Foundation, in accordance with its Privacy Statement, is empowered to collect, store, use and share (with authorized users and third-party vendors) personal data, including mobile phone numbers. As stewards of that data, UTFI is committed to protecting the privacy of UT students, faculty, staff, donors and friends, and to honoring their individual communication preferences.
This policy is designed to honor UTFI’s commitment to privacy, in adherence to applicable state and federal law, while maximizing efficiency and effectiveness in communicating with constituents about important matters relating to UTFI’s mission.
